Planning Security Projects
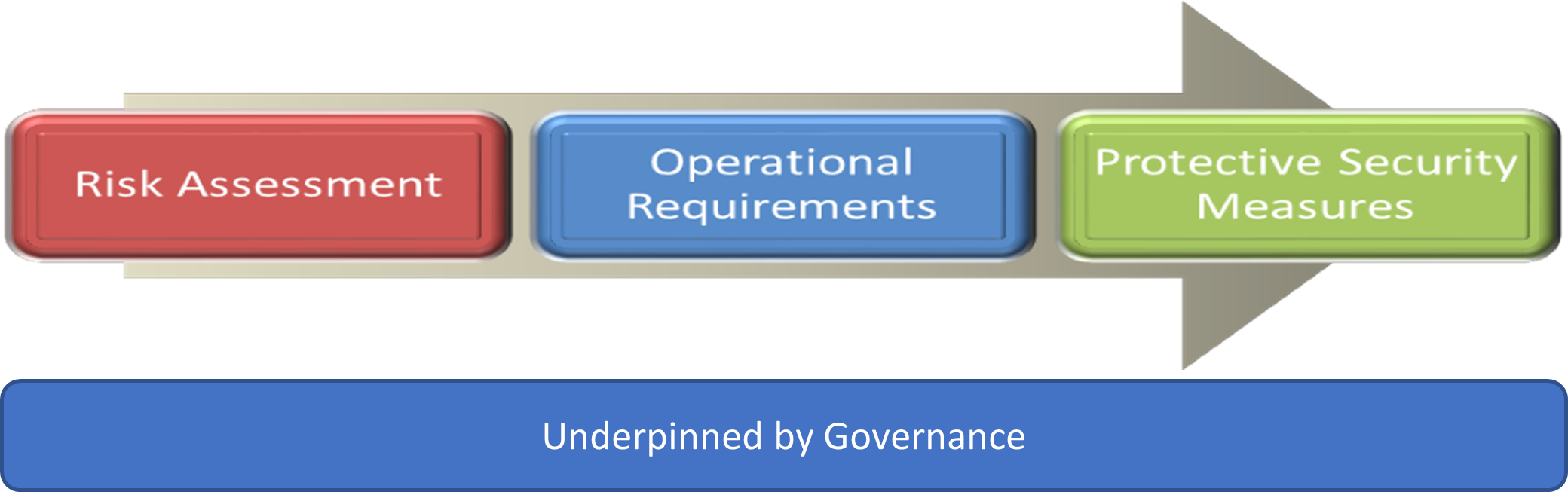
Whether a new build, upgrade or retrofit, there are some fundamental stages that any project must follow to successfully deliver proportionate security measures. This is the established NPSA methodology of:
Key messages for new builds
- Although security may not necessarily be the primary focus in new infrastructure projects it is essential that security risks are identified early in the project so that sound decisions can be made about how they will be treated.
- Security must be considered at all stages of the project and must not be thought of as a separate entity that can be addressed later in delivery by a specialist team in isolation.
- A clear governance structure to map out responsibility for decision making and risk ownership is required to successfully deliver security.
Information Management
Information Management is hugely important during the lifecycle of a built asset. It is just as important during the build phase as it is once the asset is operational. Because loss of control of information at this stage can have a detrimental impact to the security of the built asset.
It is important that an information handling strategy is established, and we recommend the following ISO 19650-5 and the additional advice NPSA have produced on adopting a Security-Minded approach to Open and Shared Data.
Information Management is particularly important on sensitive projects. The flow chart in the ISO 23234 2021: "Planning Security Measures in the Build Environment" and "Introduction BS EN ISO 19650-5:2020: "Security-minded information management" will help determine if a project is sensitive:
A Built asset should be considered to be sensitive if it:
- Forms part of the critical national infrastructure;
- Fulfils a defence, law enforcement or national security or diplomatic function;
- Is a commercial site involving the creation, trading or storage of significant volumes of valuable materials, currency, pharmaceuticals, chemicals, petrochemicals, or gases;
- Constitutes a landmark, nationally significant site or crowded place; and/or
- Is used or is planned to be used to host events of security significance.
Governance
The next stage is to identify who is accountable for security risks, NPSA recommend that there is a senior board level owner accountable for security. See Good Governance for more information.
The senior accountable security risk owner will need to determine who in their organisation is responsible for security and determine whether specialist security consultants are likely to be required. If security consultants are required, we recommend following the advice in Procuring the Services of a Specialist Security Consultant.
The governance of the whole lifecycle, including the operational phase, needs consideration at the project planning stage.
NPSA have identified a requirement to offer clear security advice to those involved in the commissioning of major projects and have produced major infrastructure projects - security considerations for clients.
Risk management process
The NPSA risk management process is as relevant to new build infrastructure projects as it is to smaller security projects and security upgrades. The risk management process covers all aspects of risk assessment including risk identification, risk analysis and risk evaluation. Prior to starting the risk assessment part of the process, it is essential that there is an understanding of the parts of the built asset that needs to be protected. Once these have been identified they should be categorised and prioritised. More information can be found at Protective Security Risk Management.
Operational Requirement
Once the security risks which need to be mitigated have been identified the measures for mitigating those risk should be selected following the Operational Requirement Process (OR).
Security deliverables in the project lifecycle
Although there are several methodologies defining the stages in delivering new build projects, the one most commonly used is the one defined by Royal Institute of British Architects (RIBA). The RIBA plan of work organises the process of briefing, designing, constructing and operating building projects into eight stages. NPSA have worked with RIBA to produce a security overlay highlighting the key security considerations at each of these stages. This is the first time that security deliverables have been officially mapped to the plan of work by RIBA.
RIBA has published the overlay on their website:
Security Overlay to the RIBA plan of Work
An illustration of the Security Overlay to the RIBA Plan of Work is available at the end of this page, together with a link to download the full guidance.
The guidance in the RIBA Security Overlay to the plan of Work is structured around 4 key security deliverables required in any project. These are:
- The security risk assessment
- The security requirements
- The security strategy
- The security plan
The guidance provides advice on when the security related tasks should take place and who should complete these tasks at the different stage of the RIBA process and provides some general advice on security measures that should be considered during the build. There are other standards and guidance products that map security deliverables to project planning stages, all tend to use slightly different terminology and provide varying level of detail but align to the basic process outlined in the RIBA Security Overlay. One which provides slightly more granular detail of security processes is ISO 23234 2021: “Planning security measures in the built environment”, which lists the security deliverables at each stage of the project lifecycle. NPSA has produced a short guide to the ISO 23234: 2021.
Illustration of the Security Overlay to the RIBA plan of work
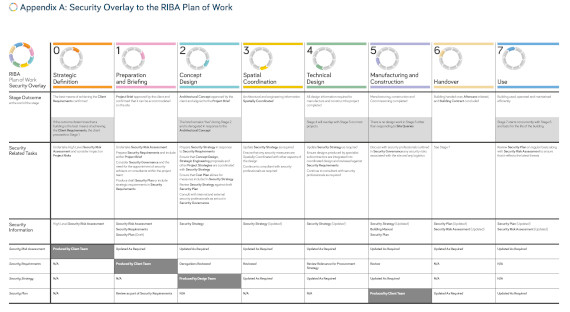
The full Security Overlay to the RIBA Plan of Work

Further Information

NPSA (as CPNI) worked with CIOB to develop “The Role of Security in the Construction Industry” the report outlines six principles of a “security mindset”, which will allow a construction manager to demonstrate their ability to identify, assess and manage site security issues. There’s also a practical guide to delivering security compliance, with a checklist examining governance, personnel, physical security measures and cyber security.




